It’s now possible to securely share variables and other sensitive fields via Directory / Git Sync!
Whether collaborating with a team or simply backing up your workspaces, you can REST 😉 easy knowing your secrets are safe. There are a few different features that make this possible, so let’s dig into them one by one.
Encryption is the main element behind sharing secrets. Without it, you’d be exposing your secrets to the world as plain-text. 🙈
The new
secure(...) Template Function
can be used to encrypt any portion of text within Yaak—anywhere environment variables
are supported.
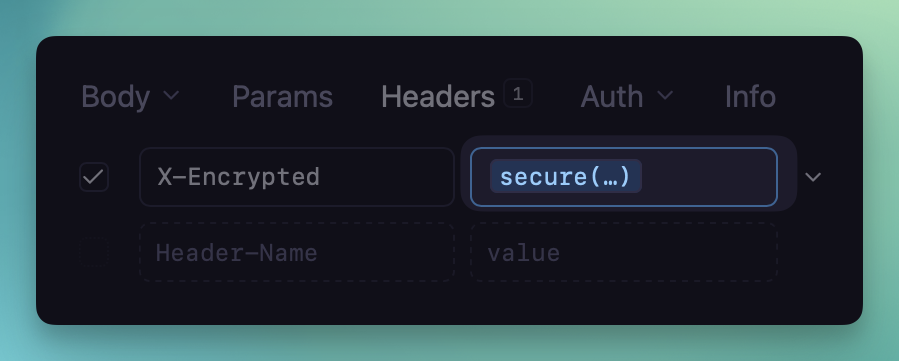
Using the secure(...) function within a header value
Encryption must be enabled for each workspace, which will generate and store an encryption key using your host OS’s keychain. Back this key up and share it with your team, as it will be necessary to access secure values on other devices.
Closes Secrets Encryption
To avoid remembering to use the secure(...) function, Yaak will use a secure input when
it guesses that a value may contain sensitive text.
Fields like passwords or bearer tokens are obviously sensitive, but Yaak will also try to
guess headers and other fields (eg. a header named X-Token).
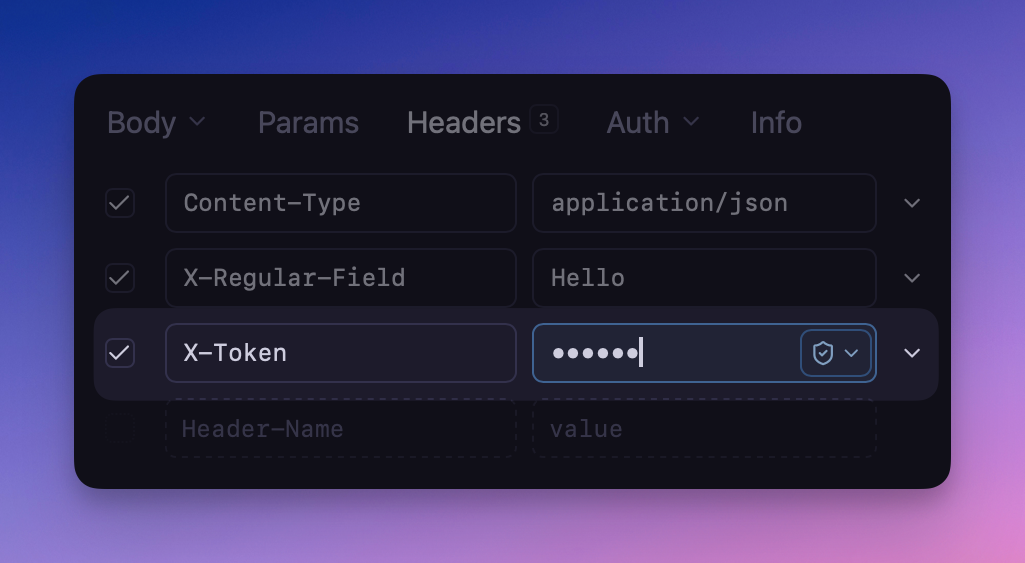
Potentially-sensitive fields will automatically use secure input
Environments were previously excluded from directory sync to prevent accidentally exposing sensitive values to Git or other tools. With the new encryption feature, environments can now be marked as “sharable” which will cause them to be included in data exports and directory sync.
When encryption is enabled, any variable added will automatically be encrypted, and Yaak will provide a stern warning if a public environment happens to contain unencrypted values.
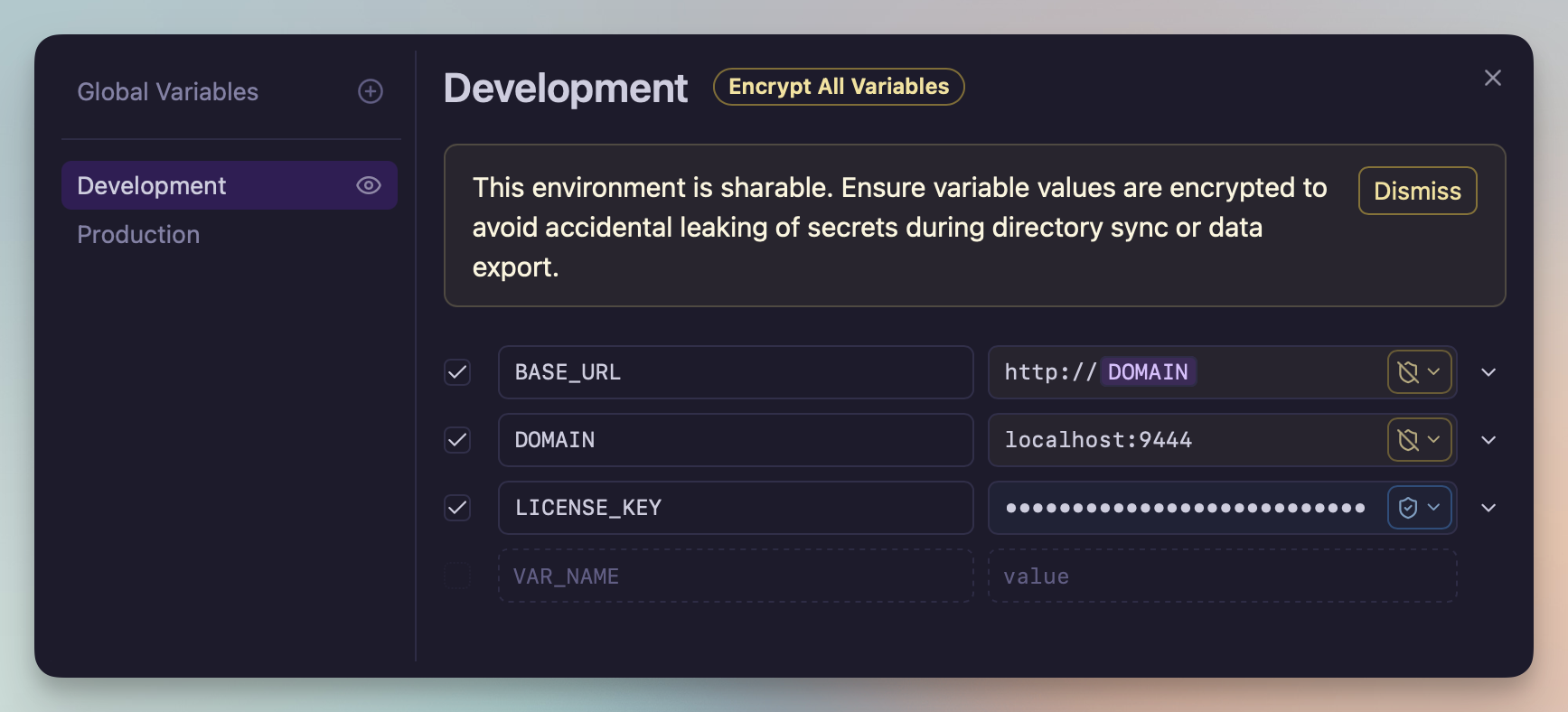
Warning when a sharable environment contains unencrypted variables
Closes Environments in directory sync
Secure values needed to be usable within template function arguments, so I made it happen. Yaak now also supports nested template functions and variables!
It’s now possible to chain functions to do useful things like get the hash of a password.
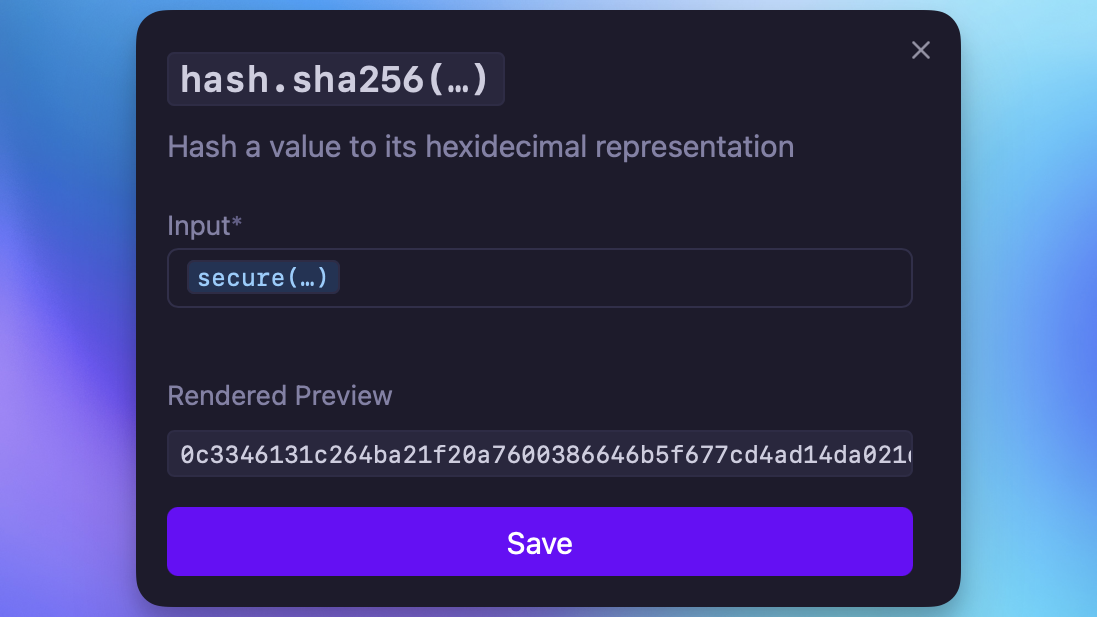
Including a secure value within a hash function
application/javascript return JSON? for websocket requests with no query paramsFOREIGN KEY constraint failed during some sync and import operationslibdbus for accessing Linux secret-servicehash.sha256(fs.readFile(...)))